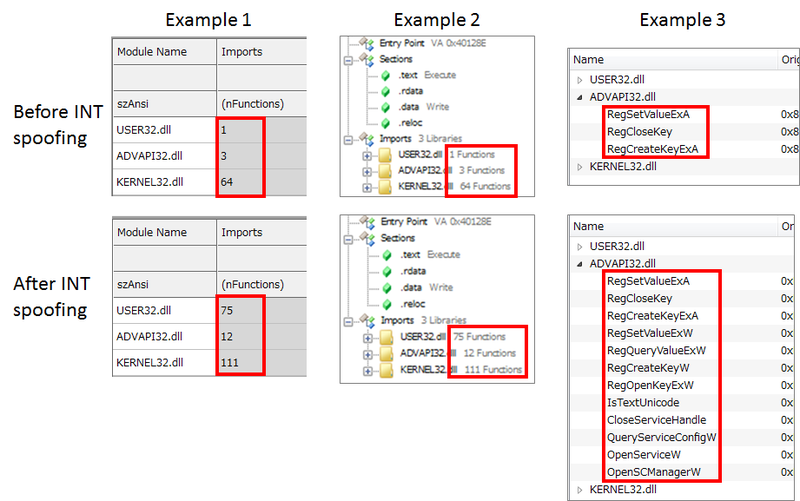
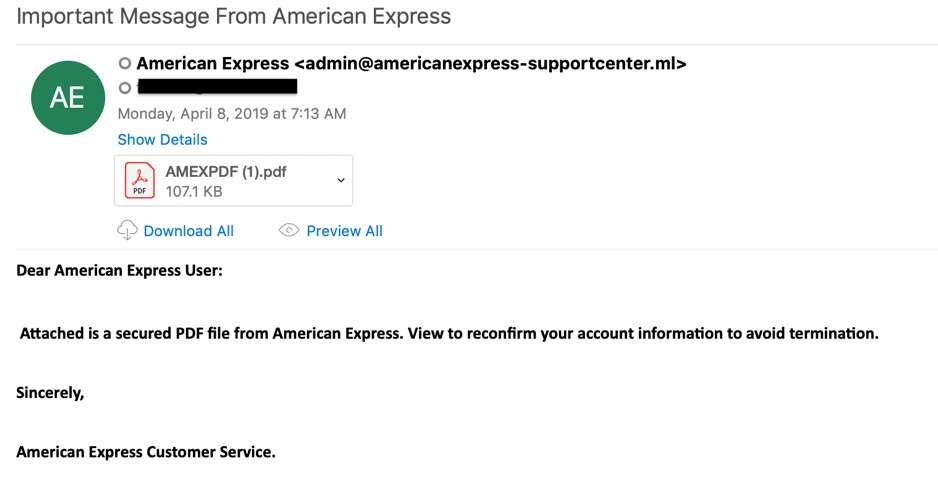
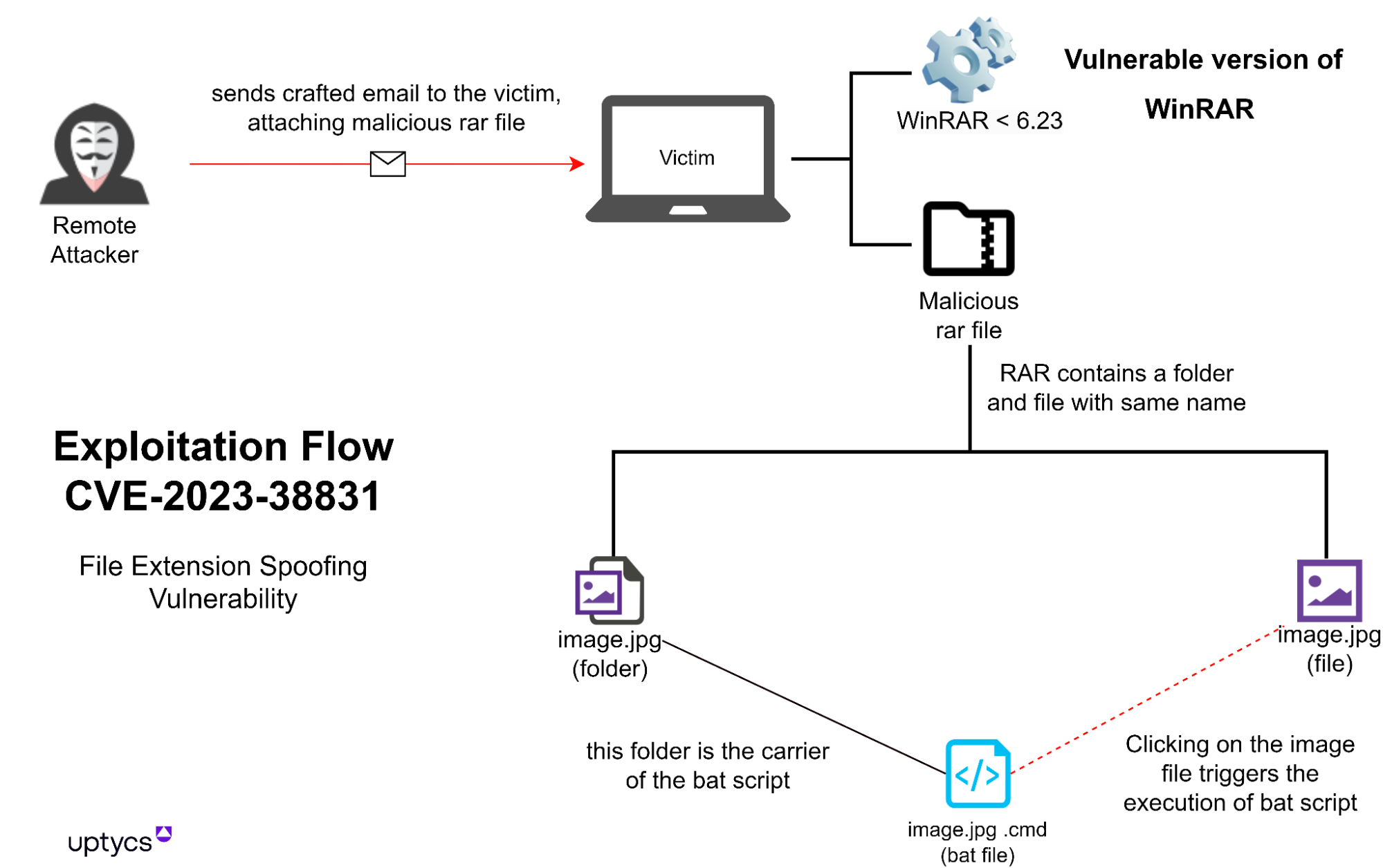
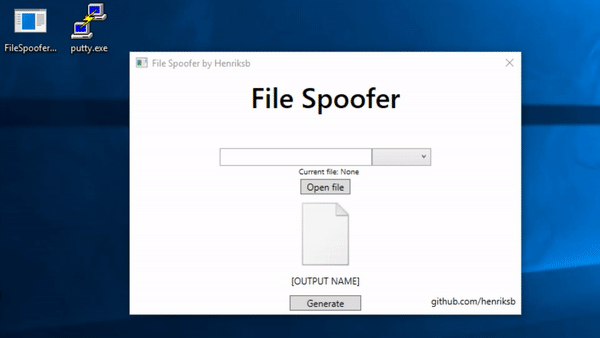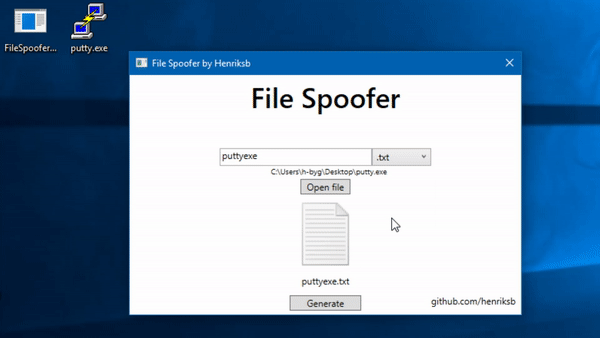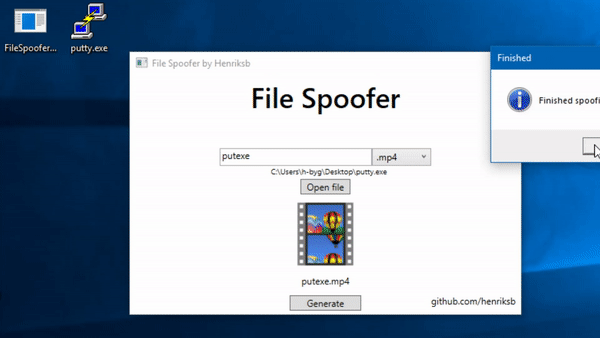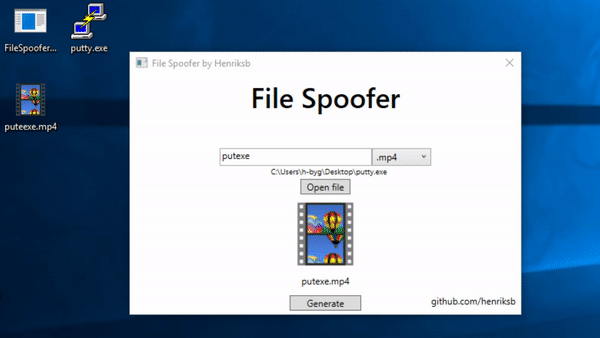
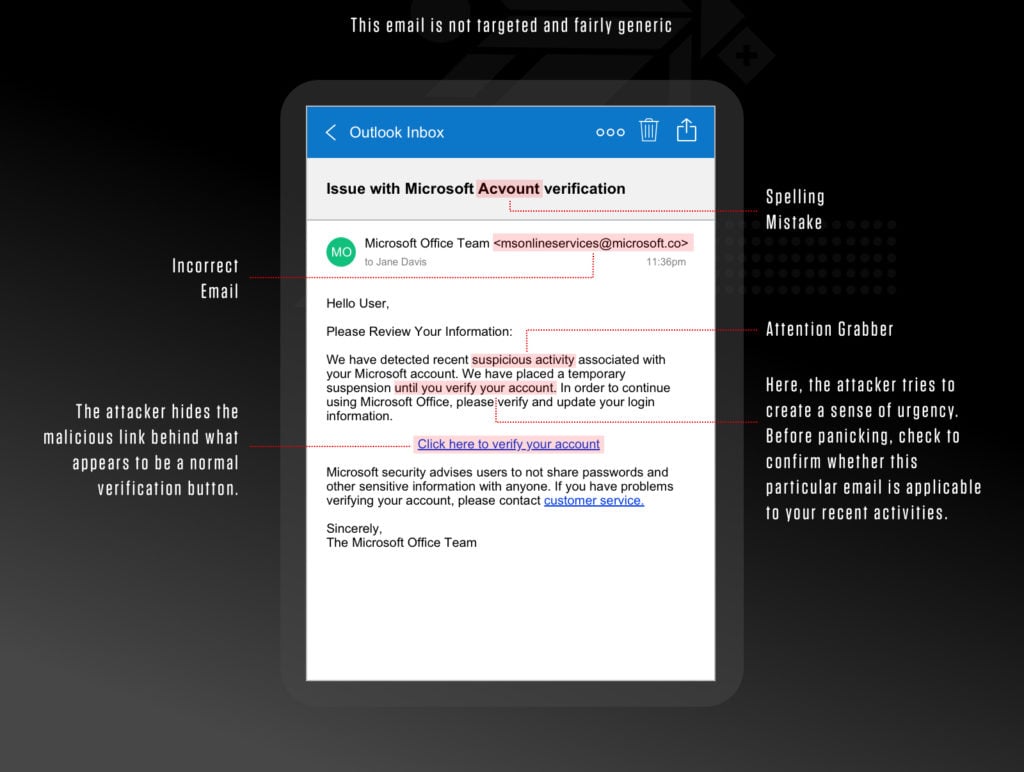
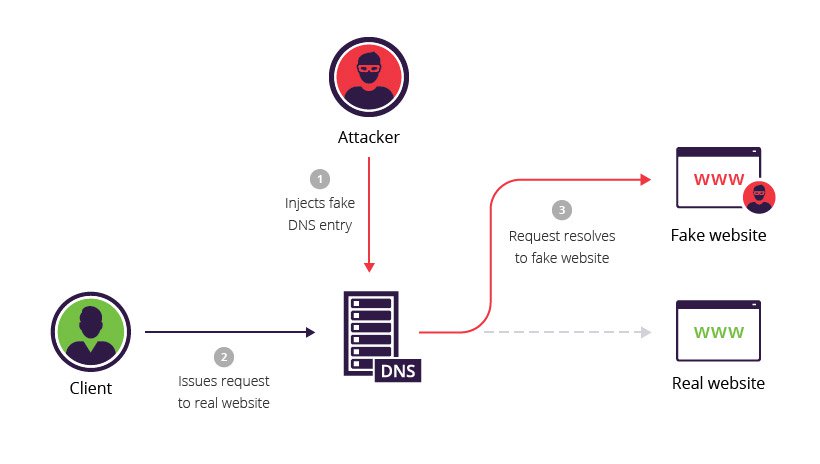
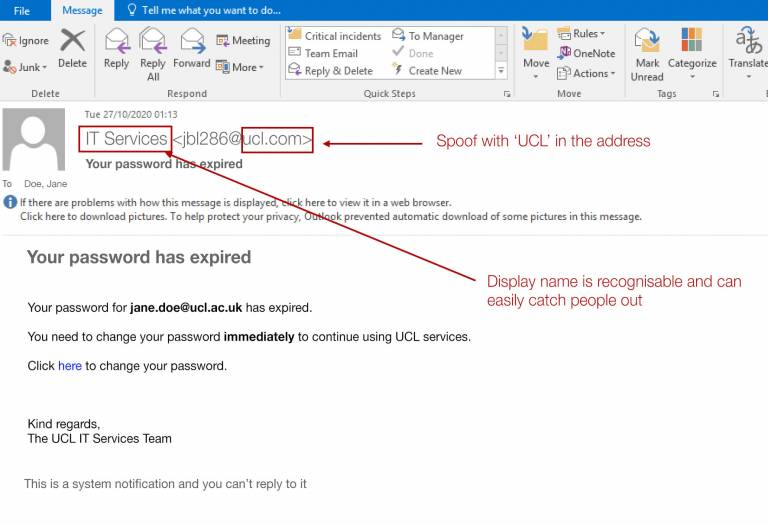
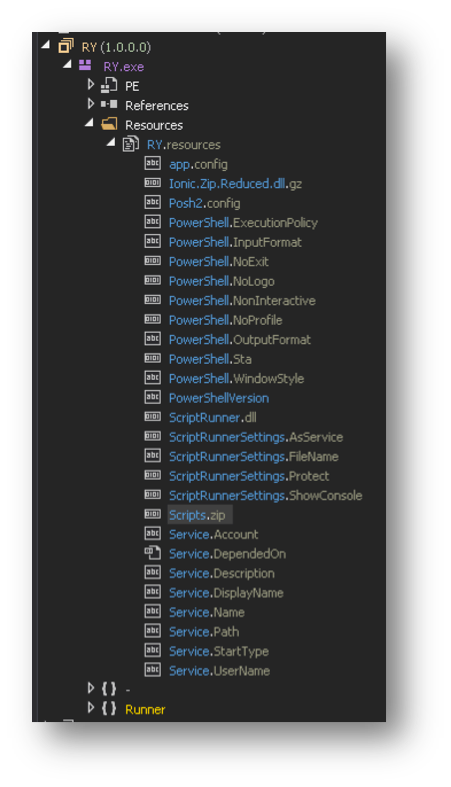
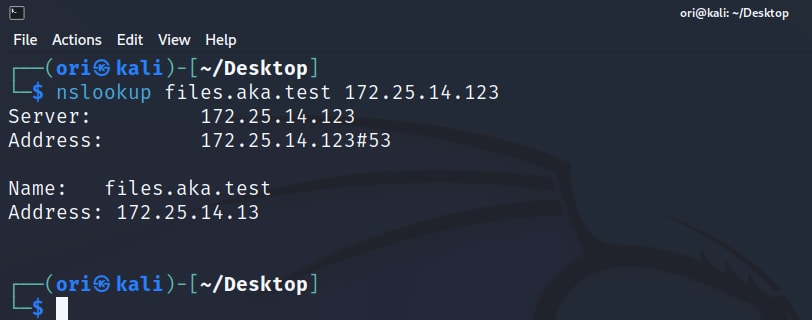
Group-IB Threat Intelligence on X: "⚡️Group-IB Threat intelligence discovers a new 0-day in #WinRAR used to target traders #CVE-2023-38831 allows TAs to spoof file extensions and hide the launch of malicious script
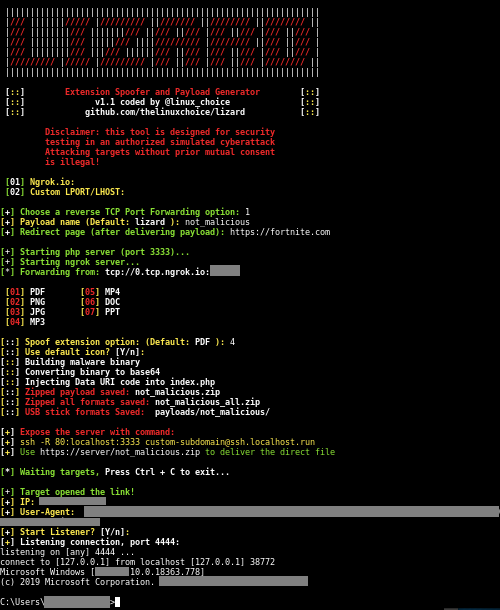
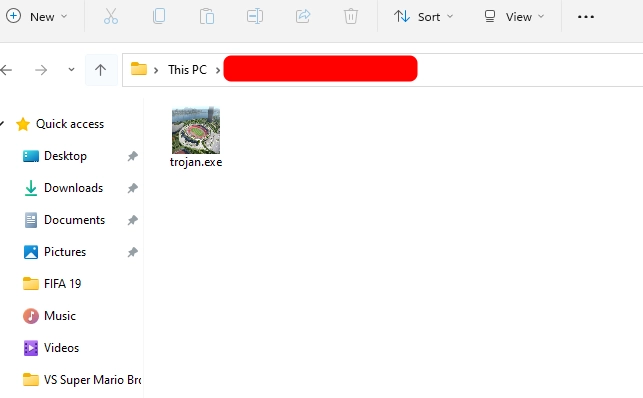
Binni Shah on X: "Lizard : Extension spoofer and reveser shell generator (Malicious file generator using RTLO technique to spoof extensions) : https://t.co/RgRuAA16ue cc @linux_choice https://t.co/GD87KDbPNF" / X
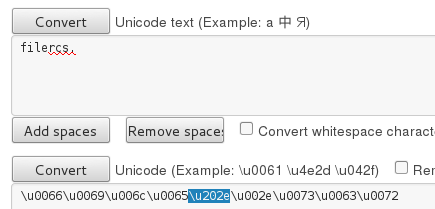
GitHub - moom825/batch-extention-spoofer: spoof an extension of any file by using U+202E Unicode character
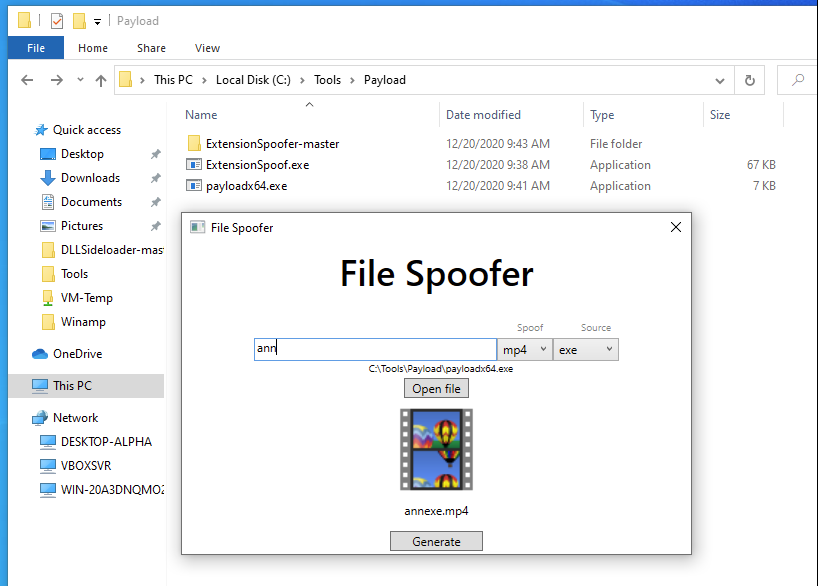
GitHub - Loubaris/Extension-Spoofer: Spoof your payloads/codes extensions into safe extensions | FUD